A post operation, as the name implies, is a type of processing that is applied to the image after the main functionality is applied. it involves storing the image in a third party storage service. Post operations can be created and configured through the control panel by going to the post operation section, and clicking on create which will show the creation wizard :
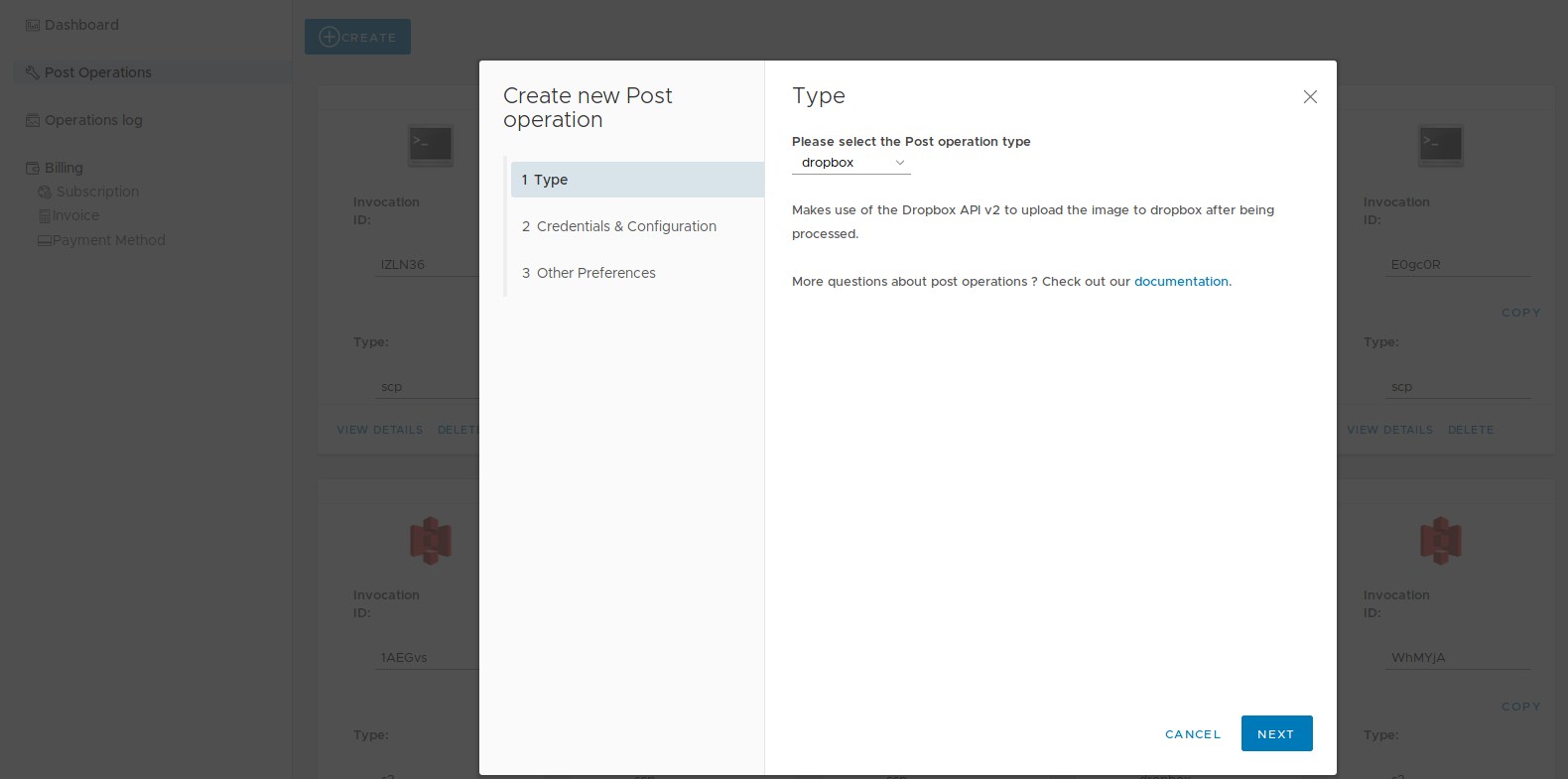
During the post operation creation, you are going to need to provide access credentials to your third party storage as service, as well as some information about where to store the image exactly. Optionally, you can also configure how the image file will be named. Once the creation process finishes, you will see a confirmation message as well as the post operation card which contains the invocation id:
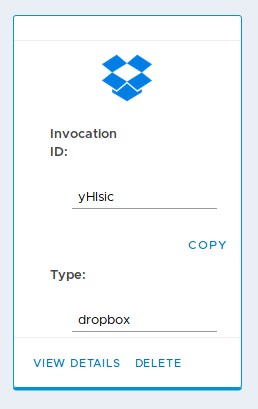
You can then use the invocation id in the X-PostOp-Id header.
As mentionned previously, post operations are only relevant in the context of Async endpoints.
Post operation types
More details can be found in the integrations section
You can contact us through the support form in the control panel if would like to add a third party integration. We don’t promise that it will be considered for implementation, but we will seriously evaluate your request.
File naming conventions
File naming convention denotes the naming pattern that may be applied when copying the file to the configured storage. Each post operation has a file naming configuration step that you can use to choose a naming pattern for your files. If none is chosen, then random names of 10 charachters will be applied.
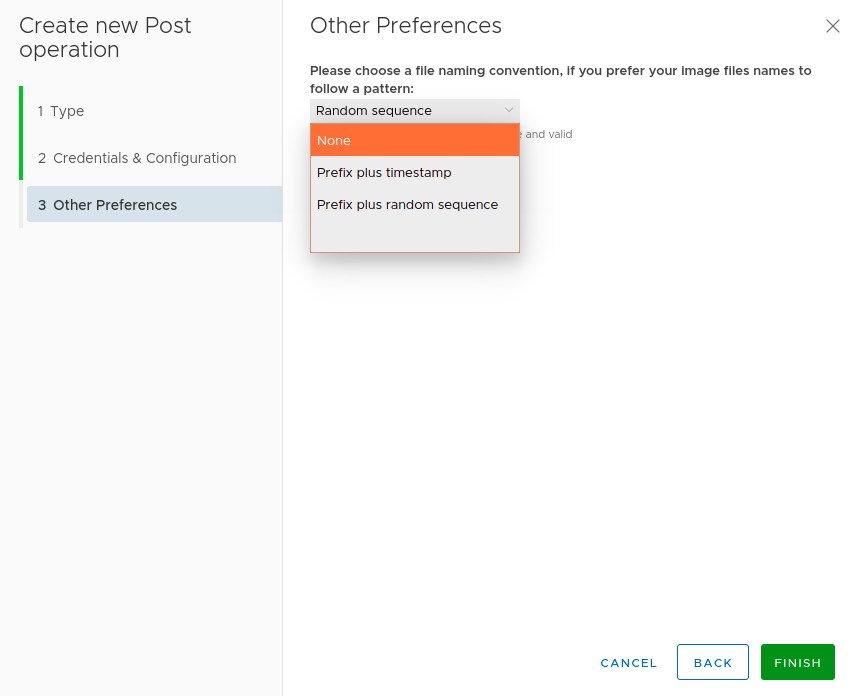
Prefix plus timestampwill add the timestamp at the moment of copying the image to a prefix of your choice (e.g myimage_1562609732818.jpeg)Prefix plus random sequencewill use your prefix in addition to 10 random charachters sequence.
Post operation credentials security
We are aware of the sensitivity of the credentials that you may provide to imager200; for this reason, we are taking several security measures. First of all, we are storing the credentials in a separate Vault where they are safely encrypted. Second of all, once you create the post operation, the credentials are never sent back to the front end, and therefore inaccessible to malicious scripts or attacks. We are also implementing several security measures like CRSF attacks protection and encryption to protect against attacks and wrongdoers.